One of the most insidious tools within the cyber-criminal’s toolbox is malware, especially the form that invades your computer and reports back your every keystroke for further processing down the line. AI-driven software routines can quickly ferret out your private login and password combinations, such that it is only a matter of time before the crook “monetizes” his ill-gotten information. The sad part about it is that you may be in the crosshairs of one of these crooks and not even know it.
Malware technology, however, never rests on its laurels. Its proponents are always innovating and searching for easy targets for the next wave. It is no wonder that the users of these tools have fastened onto cryptocurrencies, as the latest trend that needs to be ridden for all it is worth. News has now surfaced regarding a new form of malware that uses the anonymity of the blockchain to achieve instant monetization by skipping traditional steps in the process.
Take a look at the picture below and see if anything looks suspicious to you:
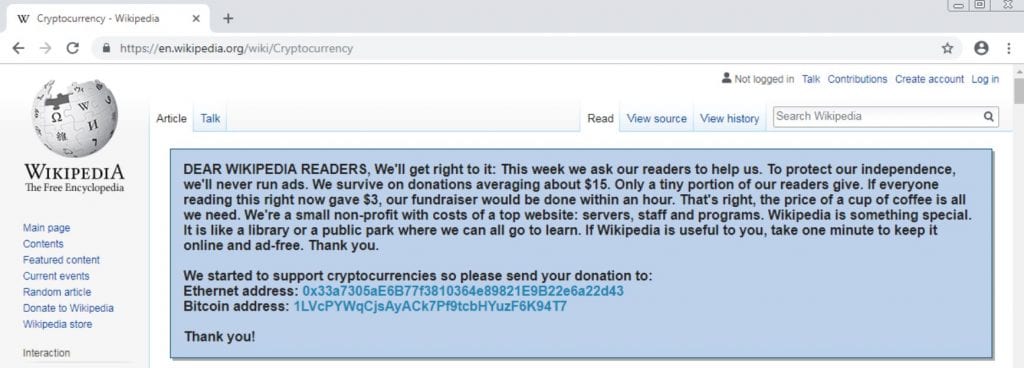
Example of Malware Fraud Source: Wikipedia
Do you give up? If you were into cryptocurrencies and felt the need to support Wikipedia, would you send your ETH or BTC to the addresses embedded in this plea for patronage? The crypto addresses, believe it or not, belong to the crooks. This new strain of malware literally sits in your computer until you visit the Wikipedia website. When you do, it quickly swings into action, replaces the addresses or inserts the above verbiage, and then, this version magically appears on your screen.
The malware also has the ability to modify Google searches, such that ads that the crooks have doctored will suddenly appear front-and-center at the top of the page. Google charges a hefty fee for that privilege, but fraudsters have found a clever way to bypass these controls and post whatever scheme might draw you in for immediate fleecing. Never underestimate the capabilities of today’s modern conman.
By the way, the malware bad guys are not deliberately singling out Wikipedia for its “contribution con”. Per one security professional:
It’s not just Wikipedia that will start sprouting scam crypto addresses though. The malware is designed to replace addresses where it can on a range of sites.
This incidence is not the first time that crooks have focused on cryptocurrencies. Malware users have been targeting cryptos for a few years, but some analysts feel that their attention span may soon wane, due to the recent meltdown in valuations. Previous versions embedded themselves in the clipboard area of your operating software. If and when you copied your crypto address, the malware would substitute their address for yours. Are you are still waiting for a payment that never arrived?
There has also been cyber-tactics directed at mining, as well. In a ruse called “crypto-jacking”, illicit miners secretly and by deceit install their malware on a host of computers, which they soon solicit to perform complicated mining calculations for their crypto-coin of choice. The victims are unaware, until their monthly utility bill arrives with an enormous amount due. Insiders claim that the popularity of this hijacking scheme has declined measurably, again, in line with declining coin values.
Do not expect malware users to depart the cryptocurrency scene any time soon. Tigers like these know how to change their spots quickly and return for more.
